Aurora is the identity risk intelligence layer that reveals who is using which AI tools across your organization without breaking existing IAM or SSO workflows.
What is Aurora?
Aurora provides high-fidelity visibility into AI tool usage by correlating signals across browser telemetry, network logs, or emails, all while keeping processing and data residency entirely inside your cloud. It equips identity, GRC, and security teams a single source of truth for AI adoption—and related use of developer, HR, data, and financial systems—without disrupting users.
Why use Aurora?
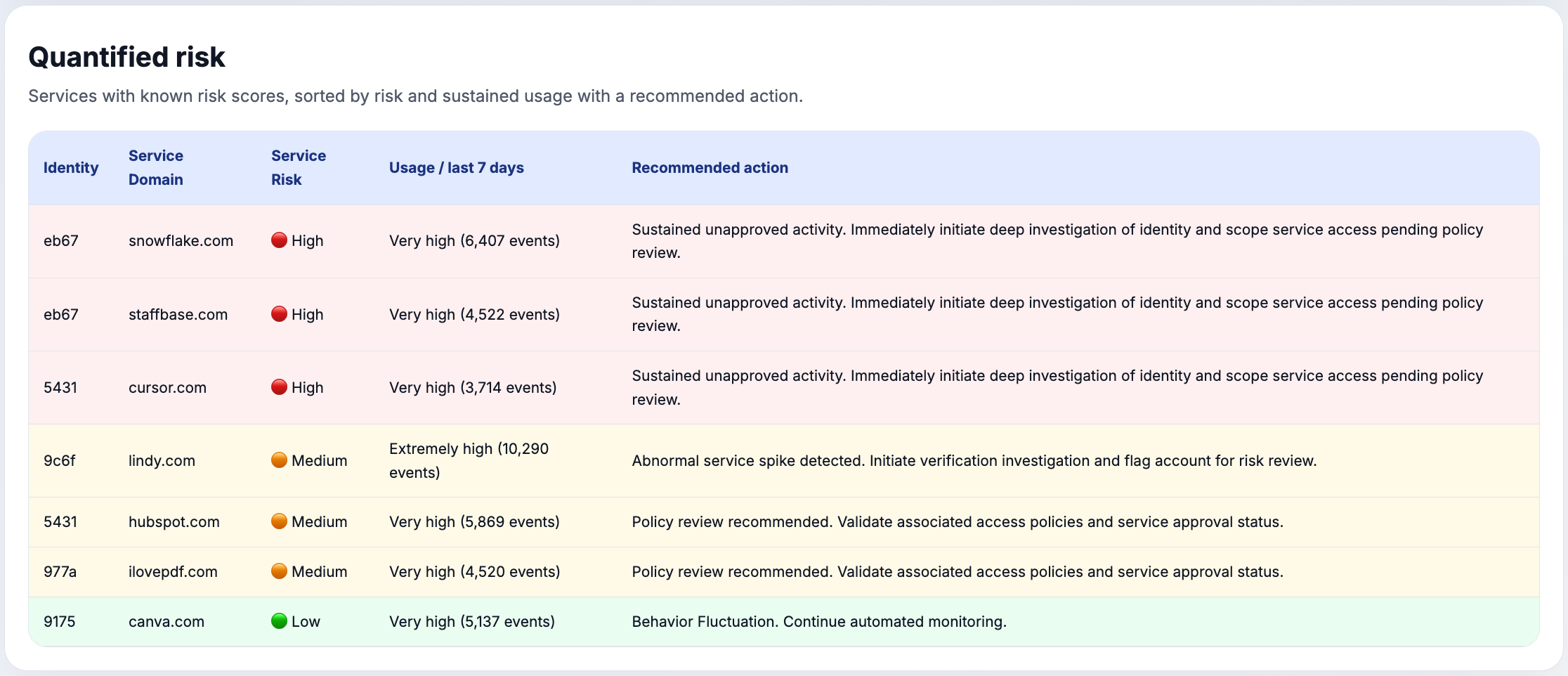
Organizations struggle to answer the foundational question: who is using which AI tools, and how? Existing shadow-IT workflows rely on fragmented signals in spreadsheets, SIEM queries, and endpoint reviews—leaving blind spots, governance gaps, and unmanaged accounts across AI products, developer, HR, data, and financial systems. Aurora replaces that manual effort with a unified, trustworthy model of AI usage mapped to real identities while keeping its primary focus on AI adoption (the most challenging problem today).
- Close blind spots around AI tool adoption and data exposure with consolidated telemetry.
- Reduce compliance and governance gaps by continuously surfacing unmanaged identities.
- Eliminate redundant investigations across SIEM, gateway, and endpoint tools.
- Lower operational overhead by automating correlation instead of manual audits.
Here is what combining all signals looks like:
What does Aurora include?
Aurora is a tightly integrated stack built to answer who is using which AI tools, developer, HR, data, and financial systems—while keeping all processing in your environment.
- Usage Intelligence Engine: Correlates browser telemetry and network signals to attribute AI and SaaS usage to real users with high fidelity.
- Browser telemetry: Collects endpoint signals for visibility into AI service interactions without disrupting IAM or SSO flows.
- Network-derived discovery: Ingests logs from gateways, proxies, and SIEMs to uncover unmanaged accounts bypassing SSO.
- AI Service Knowledge Base: Normalizes traffic patterns and enriches findings with service-specific risk context.
- Remediation workflows: Surfaces unmanaged identities and risky usage with actionable notifications via Slack, Teams, or email.
- Privacy and residency controls: Ensures 100% customer-side processing with configurable retention and zero data exfiltration.