How Aurora works
Aurora runs entirely inside your cloud (or on-prem environment) to ingest browser telemetry and network logs into a single, trustworthy view of who is using which AI tools—as well as developer, HR, data, and financial systems—without touching IAM or SSO flows.
Architecture diagram
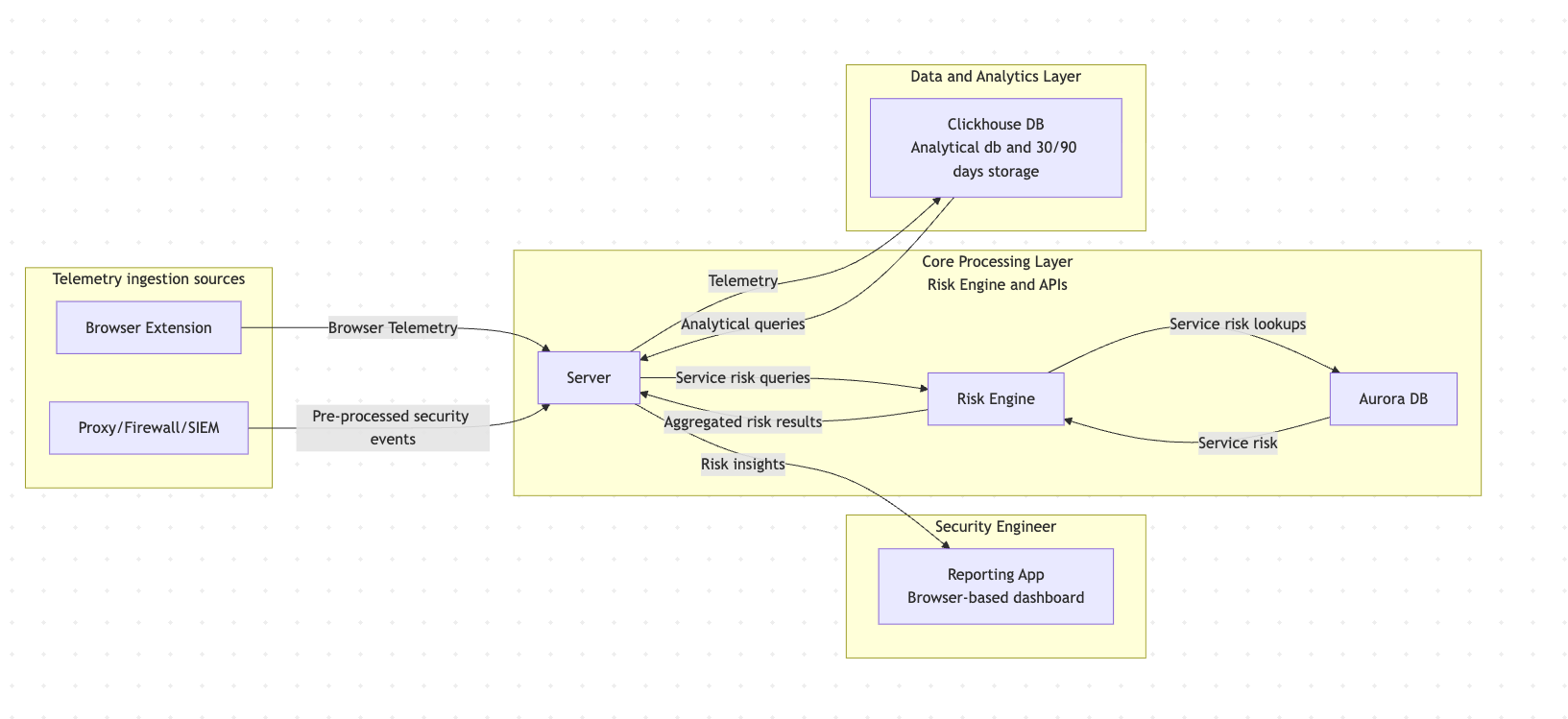
System overview
- The browser extension captures outgoing requests, tags them with a persistent
identity (uuid), and posts them to the/ingestAPI. Through collectors or workflows, logs from proxies, gateways, or SIEMs are also posted to the/ingestAPI. - The server supports two main uses: ingesting telemetry and exposing APIs for the reporting app, some of which call the Risk Engine. This runs in a Docker container.
- The server exposes an ingest endpoint,
POST /ingest, which streams each payload into ClickHouse using theJSONEachRowformat and rejects non-POST methods. You can read more here. - Storage of raw events happens in a ClickHouse database with information about the identity,
method,url, and millisecond-level timestamps. This runs in a Docker container. - Aurora DB is Aurora’s proprietary service risk knowledge database. It is a curated and enriched knowledge base that combines multiple external sources with our own research.
- The Risk Engine builds on top of Aurora DB, mapping identities and service usage patterns to specific (AI) services while filtering noise and enriching requests with risk context.
Data flow overview
- Telemetry collection: Logs are ingested either through the installed browser extension or via the ingest API.
- Identity correlation: Identities are linked to usage and service risk to uncover managed and unmanaged accounts.
- Risk evaluation: The risk engine scores findings based on factors like service category (e.g., AI tools), the service itself and its embedded risk, usage, or abnormal behaviours.
- Actionable outputs: Results stay in your environment for dashboards, alerts, and downstream workflows.
Aurora does not connect to IDPs or HR systems (as of today); masked identities (e.g., UUIDs) are sufficient to detect and map risk, supporting Aurora’s privacy-first design.